Thwarting Malware As A Service - Blocking Google
:date: 2023-12-17 08:16 :tags:
One of the things I love about ChatGPT is that for about 90% of my usage, it immediately became a superior replacement for the corrupt cesspit that is web search. In the past, if I was experiencing an emergency that required me to know, say, the various evolutionary stages of of Koine Greek phonology, I'd have to ask a search engine and then fight with a bunch of awful people doing awful things. Things related to SEO — search engine "optimization". Avoiding search engines is now so plausible because the weights in the GPT models effectively (enough for me, 90% of the time) encapsulate what I need to know.
Cutting out Google — who now proactively avoids the creed "Don't Be Evil" — is a Good Thing. If you go to ThePage on my website, you'll see that the "search box" I always use has some special properties. First, it is controlled by me. Second, it does not reveal intermediate typos as I type. Third, it does not include Google as an option. Every time ThePage is loaded, a random lesser known search engine is selected in a quixotic effort to resist the monopsonistic pressure of selling myself out to The Search Engine Which Is Evil.
But sometimes, if you can limit the raping, Google's services can be useful. My solution is to use what I call the "Google Desktop Client". Normal people call it "Chrome". I prefer using Debian approved Chromium (but it weirdly doesn't support screen sharing on Google Meeting, so do what you have to do). If I'm ever going to be using a Google account for anything, I will always be using a Google only browser. And I will use that browser for nothing but Google business.
That leaves us with (what should be) normal non-Google web browsing. For that I use Firefox. Firefox itself is a cesspit of corruption and a scandalous insult to one's safety and dignity. This can, however, be greatly ameliorated with a browser add-on called uBlock Origin. I'd say that this browser plugin effectively removes a solid half of all the garbage that your web browser would otherwise enthusiastically gobble up and assault you with.
One thing that I have been increasingly annoyed with is Google's Federated Identity pop-ups. This is their One Tap "user experience". At this time, this incredibly aggressive malware infects a very large percentage of mainstream websites. It seems that half of the links I go to these days require an extraneous click to dismiss this stupid box which is exhorting me to reveal everything I've ever done with the internet to Google and any one else with money.
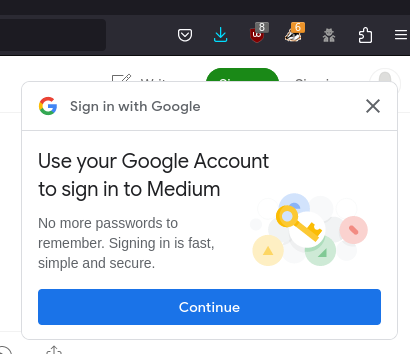
On this creepy page, Google describes how truly Evil they are prepared to be to deface the website you're trying to see with their garbage. But this is an interesting bit.
This section only applies when FedCM is disabled, when FedCM is enabled the browser displays user prompts on top of page content.
This made me wonder, can I turn this off in the browser? Maybe. But I sure couldn't find anything mentioning it.
Which brings us back to uBlock Origin. While the Evil minions over at Google have cleverly managed to bypass normal pop-up and uBlock filtering, that's not the end of it. It turns out that you can go to the uBlock Origin add-on settings and then to My filters. Add this filter.
||accounts.google.com/gsi/*$xhr,script,3pThat was a little cryptic for me, so here are some very insightful details My Robot BFF told me about how/why this should work.
||: This indicates that the filter should apply to a domain and its
subdomains. In this case, it applies to accounts.google.com and any of
its subdomains.
accounts.google.com/gsi/*: This specifies the path. It targets any
resource under the /gsi/ directory on accounts.google.com. The
asterisk * acts as a wildcard, meaning it will match any resource path
that starts with /gsi/.
$: This is a separator that divides the domain/path specification from
the filter options.
xhr,script,3p: Options for the filter.
xhr: Stands for XMLHTTPRequest, which is a type of network request
commonly used for loading data in the background (AJAX requests).
script: Targets script requests.
3p: Stands for third-party, which means this rule applies to
requests that are made to accounts.google.com from other domains (not
from accounts.google.com itself).And it does seem to work! At least for now. Maybe this technique can help you solve this problem and/or others like it.