Mobile Security Is An Oxymoron
:date: 2016-11-30 08:27
Ok, so I'm a very weird guy, I can see that. Mobile phones can be very handy, I can see that too. Combining those things it turns out that mobile phones are still pretty useless to me personally. That fact, I concede, is strange. I participate in less than a dozen actual telephone conversations a year even when including the hardwired telephone sitting in front of me on my desk at work. I can not remember a telephone call that would not have been better served in an email. Many of my telephone calls involve waiting on hold for dozens of minutes. Today, the fundamental advantage of telephones isn't the frequency-clipped disembodied voice you can hear, it is that the rudeness and imposition of interrupting someone are usually overlooked. But not by me.
Ok, so unless you just like hearing the sound of other people's voices nattering away while you're in the grocery store, and I understand there are many such people, the whole 19th century telephony thing is not extremely compelling. But what about all the other great stuff? Throwing enraged birds into pigs? Everyone loves that, right? Nobody knows how to use a paper map any more so it's not like it's even optional, right? Everyone wants to know what their friends' lunch looked like and gleefully stalks Pintergramerbook to find out, right? I could go on and on, but, folks, I'm sorry, I'm as aware of the benefits of technology as anyone and I do not find smartphones compelling. Sorry.
I can confidently surmise that I had my Sharp Zaurus SL 6000 before you had a smart phone. That brilliant pocket computer highlights exactly why I find modern small computers so uninteresting. On the Zaurus I could easily open a terminal. It ran a proper Linux kernel and I had full root permissions. I could run a Python interpreter in the normal Linux way. I could install any Linux software, Vim for example, and write my own. I could tape it to my Roomba and steer with it over wifi SSH. I felt like I was in control. But Android revoked almost all of that control. Don't talk to me about the nightmare of warranty-voiding freakish rooting hacks. The necessity of such tricks is exactly the problem.

Now we come to the elephant in the room. What happens to security when you use a networked system which is controllable by clever hacks and back door tricks, but impossible to control by authorized users using ordinary methods? It sucks. When I look at almost any security measure taken by the computing systems that I feel are safe enough to use, they are almost all invalid with modern phone operating systems. For example, why do package maintainers provide MD5 hashes of packages? So you can verify things came from a trusted source. With Android, you can't verify anything of the kind, and you have no idea who is a trusted source. Or take a simple thing like user accounts. These are designed to restrict privileges so that if some software is acting in bad faith, it can be contained. Android has a disgustingly perverse privilege model that just mocks proper security. The only thing that user accounts seem to restrict with Android is the device's legitimate owner.
Blah, blah, blah. Ok, ok. There are zillions of Windows users out there who obviously don't care about terrible security and bizarre conflict-of-interest turf wars in their computers. Fine, fine. What is blowing my mind in the smartphone era are the Linux people. The acquiescence of the people who should know better is what really freaks me out.
The first iPhone I ever saw was being proudly shown off by a sysnet (systems and networking) professor, a guy who studies computer security at the highest level for a living. I remember the thought I had at the time which remains the same to this day, "Hmmm...and you're ok with that?"
[quote,Benjamin Franklin]
Distrust and caution are the parents of security.
Security is hard. In the Linux world at least 50% of knowing roughly what you're doing involves various security measures. With the advent of smartphones it seems like everyone took the opportunity to make a clean break with the truly onerous task of secure computing. By relinquishing control, even technical people seemed relieved to relinquish responsibility too. Another quick example — I asked the head computer security analyst at my university (largest employer in the 8th largest city in the USA) what he thought about phone security. His answer was, essentially, it's bad. Very bad. Ridiculous bad. Sure. Whatever. So what does he do about it? Well, nothing special really. He mostly just assumes it's insecure and behaves accordingly (lucky for him he's a professional at that). And yet, he believes that his smartphone was responsible for his Amazon account being hacked (and if anyone should know that, it is he). How did that then change his behavior? Amazingly, not much! This is typical! People who know better stop caring for some reason. I don't understand this. I haven't been able to stop worrying and love this bomb. I have never been interested in using a computer as a computer that I can't control with the full force of computer science. I don't care what magic services it provides. If I don't have at least theoretical control and it knows who I am, it creeps me out and I want nothing to do with it.
Obviously I have a lot to say about modern telephones, but at the same time, I don't. I wish I could point to the smoking gun and say, ah, here is why you shouldn't use this. But I am not an expert in these systems which are designed to prevent me from properly understanding them. I just know what I appreciate and trust about the Linux systems I do use, and I can't see any similarity to the way smartphones are controlled. For the same reasons I (and people like Richard Stallman) boycotted Microsoft operating systems for almost 20 years now, I can't accept Android. I feel vindicated that my 1999 assertion that the Linux kernel could be made usable by normal people was true, but at this point Android is worse than Windows. (Do I even need to point out that IOS is worse than Android?)
Ok, I don't like telephones. I don't like proprietary operating systems that exclude you from control, destroy your privacy, and prey on you at every opportunity. With all that baggage, in comes a new topic that is of particular importance to fancy computer people taking care with security: multi-factor authentication. Abbreviated as MFA or 2FA, this basically is about using your phone to add another layer of security to unrelated services. I think you can guess by now how I feel about that. I'm not impressed. I'm horrified.
But again, I'm not the head of some nation state's hacking agency. Although I take a serious and diligent interest in security concepts, I don't make a career of studying the dark corners of proprietary software. When I step out of the light of the non-proprietary, free software world, I am overwhelmed and terrified.
This post is just a starting point, a way to dump my rough misgivings along with some links to why someone might feel this way. Make of it what you will.
Phone Insecurity
[quote,Philip K. Dick]
Strange how paranoia can link up with reality now and then.
- An amazing article in the NYT about Chinese surveillance of your phone. "Security contractors recently discovered preinstalled software in some Android phones that monitors where users go, whom they talk to and what they write in text messages."
- Cheating at poker... damn, that's scary.
- App proves Rowhammer can be exploited to root Android phones – and there's little Google can do to fully kill it
- The real vector is bad apps. "For years, most Android malware has spread by social engineering campaigns that trick a user into installing a malicious app posing as something useful and benign." MFA still safe? Maybe for a "phone" that does nothing but serve as a MFA fob. Note that the article is actually saying the problem is substantially worse than that because now malware can be contracted from concomitant ads you wanted nothing to do with.
- UPDATE 2017-07-06: Incredible hardware attacks from repair shops.
- UPDATE 2017-09-14: I have never trusted or used devices with Bluetooth. And here is why. This "BlueBorne" attack can remotely take over iOS, Android, and any other system capable of Bluetooth. "Moreover, Bluetooth offers a wider attacker surface than WiFi, almost entirely unexplored by the research community and hence contains far more vulnerabilities." Fortunately with proper Linux you can compile the kernel yourself to have no clue what Bluetooth even is. I know this because I often do it. Too bad about Android though.
- UPDATE 2018-06-16: NYT reports on Securus Technologies' creepy surveillance service which can locate pretty much any cell phone any time. It's supposed to be for law enforcement (which itself is a bit gray) but there are reports of abuse. And, of course, here's an article on Securus getting pwned pretty hard.
- UPDATE 2019-04-17: Well, this is a doozy. This paper details a side channel attack on phones by listening to you paw at the screen through the microphone. They're getting a shockingly high success rate too. They'll be eye tracking with the camera next! This is a good time to be reminded about a potential extension of this attack where the bad guys listen through the headphones configured as a microphone. My article on that: http://xed.ch/blog/2016/1128.html
- UPDATE 2020-12-15: Here's a writeup of an exploit that takes advantage of a iOS buffer overflow issue and allows complete control over the air of the entire device. "With just this one issue I was able to defeat all the mitigations in order to remotely gain native code execution and kernel memory read and write." This means that if you just walk by this exploit in action, it can exfiltrate any sensitive data (e.g. photos, contacts, browsing history, etc) and plant malware to subvert and monitor future activity. Fun! And this is one guy who is on the white hat team pulling this off alone and letting Apple patch it. Do you think this closed ecosystem is immune to Big Brother's efforts?
- UPDATE 2021-04-16: The answer to computer security problems is generally to keep everything as up to date as possible so that lingering vulnerabilities don't make you an easy target. However, Here is a report of "New Advanced Android Malware Posing as 'System Update'". This malware is pretty much completely game over for any security or privacy you thought your phone had. What I find interesting about it is that it aggressively hides its behavior by promptly exfiltrating any stolen data (images from your camera, phone conversations recorded) in a way that the user would assume is legitimate (because System Updates often involve bloated bandwidth requirements).
MFA With Phones Is Bad
- Can we agree that whoever has complete control over your device can completely subvert MFA? Please?
- Given the history of large companies' security (Sony, LinkedIn, Home Depot, etc), if you give your phone number out to companies the odds are high that it will end up in the hands of criminals.
- What happens if your phone is lost, stolen, out of batteries, left at home, etc. — MFA using that phone is __worse__ than useless. MFA always suffers from the problem of what to do if the various components fail.
- Why is a mobile phone considered an additional factor for multi-factor authentication, but email is not? This is absurd. For some of us anyway.
- Is it multi-factor when someone uses their phone to access a service and then receives the MFA token on the same phone?
- In my AWS attack they had me before I ever would have had a chance to register MFA. In theory, they'd have had my phone as well, compromising all other MFA schemes.
- Krebs talking about a phone based MFA scam.
- Social Security security apparantly requires an insecure telephone... And rescinded!
- This bizarre article argues for phone 2FA but do carefully check out the utterly insane contradictory section "Faking Two-Factor Authentication".
- Dedicated MFA authentication devices seem like a reasonable idea. Using another computer, one which is likely to be insecure, does not.
- UPDATE 2017-05-15: Because of SS7 attacks 2FA Is Screwed. No kidding?
- UPDATE 2017-06-21: Password reset problems with phones.
- UPDATE 2017-08-31: While not completely writing off phones, Brian Krebs covers a lot of the complicated issues with phone MFA in Is Your Mobile Carrier Your Weakest Link.
- UPDATE 2018-02-06: The Reg documents an insidious case where a dude lost his BTC because the cell provider (T-mo) let the crooks transfer the phone number so they could have their way with it. Even the safeguards in place to prevent this, didn't.
- UPDATE 2018-07-20: A sobering article about the perils of placing faith in 2FA as normally practiced. "In most cases, the problem isn’t two-factor itself, but everything around it. If you can break through anything next to that two-factor login — whether it’s the account-recovery process, trusted devices, or the underlying carrier account — then you’re home free. Two-factor’s trickiest weak point? Wireless carriers. If you can compromise the AT&T, Verizon, or T-Mobile account that supports a person’s phone number, you can usually hijack any call or text that’s sent to them." And, exactly what I've been saying for years: "There's no simple fix..."
- UPDATE 2018-08-10: JWZ has a big thread about MFA/2FA. And no one is especially impressed with any of it. JWZ himself chimes in with this eternal wisdom which I live by: "'The security of this mechanism relies on nobody seeing the source code' should be setting off screaming klaxon alarms." The main point everyone agrees on is that using SMS for security is a terrible idea. Anyway, many smart people painfully sweating the security devils of detail while trying to play along with popular 2FA schemes. This affirms to me that if you dedicate your entire life/career to getting 2FA right, you might be successful.
- UPDATE 2018-08-16: OMG... Guess who else, besides me, does not use MFA with Google Android phones? That's right, Google! (According to Krebs.) So what do Google people use? They (all 85k+) use U2F which is basically exactly what I have recommended since the topic first came up (an asymmetric cryptographic key on a physical device). This particular scheme can be used by normal people for $20. This is such an improvement over MFA using a dodgy computer controlled by Russian hackers (your telephone) that I may actually buy one of these U2F devices. This particular device cleverly imitates the HID traffic and pretends to be a keyboard eliminating dodgy client interface issues. I'm a little concerned about software keyboard loggers/injectors, but in theory, that shouldn't even matter too much. This is a good system and highlights why bare telephone MFA is so sketchy. UPDATE 2019-07-22: Uh oh. Even this kind of strategy can have problems. Still it's not too bad and if this is as bad as it gets for this kind of approach, I still believe it's as good as it gets.
- UPDATE 2018-11-15: Here is an extremely helpful article that clearly explains why someone like alpha-security-pundit Bruce Schneier would say, "While [MFA] is often an important security measure, it's not a panacea." Take special note of this important point: "Neither an authenticator app nor a security key can prevent an attacker who controls your computer from taking over once you login." If you believe, as I do, that telephone computers such as Android and Apple are fundamentally compromised ab initio (i.e. they control the computer and not you), you can see how I treat phone-based MFA schemes with extreme caution.
- UPDATE 2018-11-15: Wow! I had wondered about this but now it looks like my suspicions are confirmed in this excellent but very creepy paper. Basically when you give Facebook your phone number for MFA, they sell you out to advertisers based on that number. Note page 13, "We added and verified a phone number for 2FA to one of the authors' accounts. We found that the phone number became targetable after 22 days, showing that a phone number provided for 2FA was indeed used for PII-based advertising, despite our account having set the privacy controls to the most restrictive choices." Thank goodness the other big internet companies don't do this.
- UPDATE 2019-05-02:
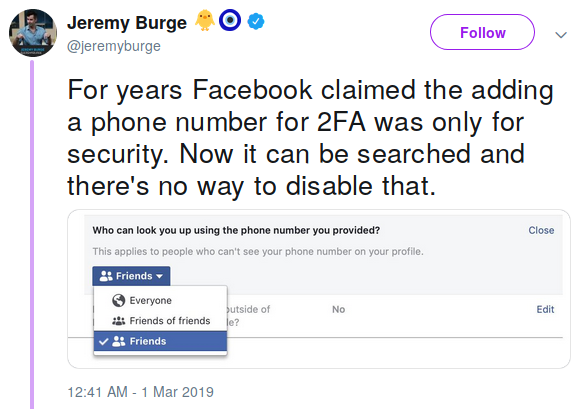
- UPDATE 2021-03-17: The most important thing the telephone you stroke does for its overlord is send you, the victim, spam. The owners of "your" telephone use legal spam-sending "services" like the one described in this Vice article which describes how "A Hacker Got All My Texts For $16". Of course since "texts" are very often a 2nd authentication factor, well, there goes that fine plan. A nifty property of this exploit is that it seems slightly more legal-ish than social engineering a SIM swap and doesn't tip off the phone's victim. You — you are the phone's victim.
- UPDATE 2021-08-15:
JWZ highlights the problem
nicely. The whole comment thread is interesting too.
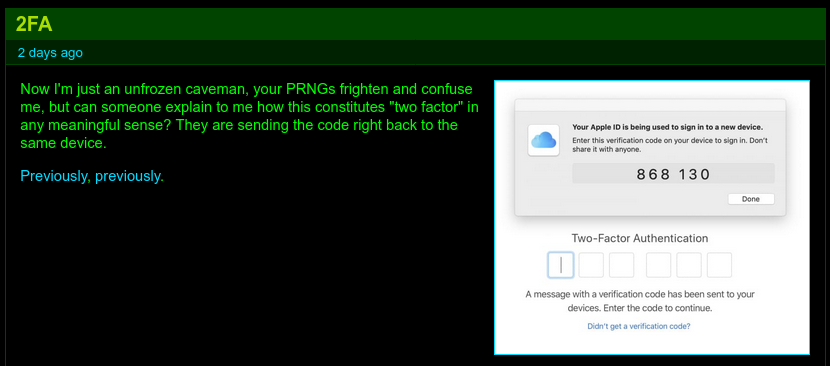
- UPDATE 2021-11-14: Schneier highlights a case illustrating how users can easily become befuddled with the other factor's challenge. This particular executive let attackers into his company by hitting "Approve" not realizing that was supposed to go — only — with a request for access by him. The comments are filled with such stories of mishandling basic cryptographic safeguards out in the real world.
- UPDATE 2022-04-15: Another report of real attacks on MFA using dumb tricks like spamming the authentication action request until the victim just acquiesces. Schneier says that "...even though there are attacks against these two-factor systems, they're much more secure than not having them at all. If nothing else, they block pretty much all automated attacks." For normal people, I would concur, but I would emphasize the "if nothing else" part because A. blocking automated attacks is possible with good security practices (i.e. better than, say, basing security on a telephone controlled by mysterious others) or, if that's not true, B. this won't be blocking pretty much all automated attacks. And since when is it ok to have "pretty much all" attacks blocked? And for these (FIDO2) biometric systems mentioned, what if your fingerprint changes (it's happened to me many times), or you get older or grow a beard? Locked out until you return to your youthful appearance? Or can it be helpfully spoofed with a photo? Ahem. A big problem with modern security is that most people think in time blocks of about the length of a telephone update support cycle. Which is woefully short.
- UPDATE 2022-06-15: Twitter this time, but you'd be an idiot to believe it's not universal. This article is reporting that "Twitter pays $150M fine for using two-factor login details to target ads". The article explains, "...Twitter obtained data from users on the pretext of harnessing it for security purposes but then ended up also using the data to target users with ads." Shocking, right? Well, no, not to me. This massive conflict of interest is why people should be much less credulous about the actual "security" enhancement provided by MFA as typically enacted in the wild.
- UPDATE 2022-09-15:
Love
this
MFA fail based on a MITM attack. It not only shows a perfectly
delightful vulnerability when putting all your eggs in the MFA basket
but it also helpfully demonstrates why SSH makes you type
yeswhen you make a first connection. Of course we can't get companies to have a clue how DNS works and we get nonsense like googleapis.com (instead of apis.google.com) so wanting them to play along with a sensible host key system seems a little unrealistic. I'll leave it with this quote from the comments which resonates with me: "Honestly, I'm shocked that it apparently took upwards of 5 years for the criminals to notice what was immediately obvious to me. Or took that long for security people to notice that the criminals had noticed."
- UPDATE 2022-09-15:
This one is so
dumb that it almost seems petty to include it. But this is exactly
the kind of shit that can get you in trouble with a false sense of
security using badly conceived MFA. The basic premise is the thief
breaks into gym lockers and steals phones and credit cards. When the
card needs the phone to authenticate, the thief has that and even if
locked, the phone flashes the access code anyway (that seems to be how
everyone has it configured). So it's fine to say that's a dumb attack
and you're much smarter than that. But is everybody at all your banks
and important services equally clever? Are you sure you've thought
through all the dumb stuff like this? This is what makes putting all
of your security into a slippery handheld device that's easy to lose
control of more than just slightly questionable.
While turning off my "display texts on the login screen" I noticed a text: "T-MOBILE SUPPORT: We noticed a new login into your account on another device. If this wasn't you, kindly reply NO." Uh... I do not have a T-Mobile account. You sure you're really ready for that minefield?
- UPDATE 2022-11-03: Sometime web services pray to the "2FA" cargo cult but they understandably don't want the considerable headaches providing that properly entails. So they outsource it to an "authenticator app". This means that instead of a patently insecure SMS channel, they rely on some patently insecure malware known as "Android" or "iOS". Even if those bad faith actors leave you alone, what exactly do you use for the required 3rd party app? Seems like the door is wide open for abuse there. And with that thought in mind, I found this article - Did You Install This Malicious Android 2FA Authenticator App? - which outlines the exact scam I'm envisioning happening in the wild.
Cell Network Attacks
SIM Card Attacks
- UPDATE 2017-06-22: All kinds of security problems with 4G VoLTE.
- UPDATE 2019-30-22: Krebs interviews a security researcher who clearly explains why tying your identity to your phone number is very, very risky. This is a follow up to another essential post from Krebs if you're relying on your mobile provider to not capriciously give away your identity.
Client OS/App Vulnerabilities/Malware
- https://support.apple.com/en-us/HT207107 Holy shit... - An application may be able to disclose kernel memory - An application may be able to execute arbitrary code with kernel privileges - Visiting a maliciously crafted website may lead to arbitrary code execution - https://motherboard.vice.com/read/government-hackers-iphone-hacking-jailbreak-nso-group[spooks love this stuff]!
- These attacks apparently exposed 600 million Samsung handsets through weak screen "keyboard" software (luckily, my ancient Samsung has a real physical keyboard, the reason I keep it). - CVE-2015-4640 - CVE-2015-4641
- A huge portion of Android installations are known to be insecure .
- List of Android Security Vulnerabilities... better get some coffee, it's long.
- So make sure you update frequently! Right? Uh, maybe not...
- It's not like AdSense is your friend on a good day. Wait until an Android trojan abuses it.
- PhD thesis of Xinxin Jin elaborates on the idea that "network programming defects (NPDs) are pervasive in mobile apps". [Her software] "NChecker detects network bugs in 99% of the evaluated apps."
- UPDATE 2017-06-26:
Wow! I knew it was bad on first principles but to see in practice
the whole rotten smartphone architecture go down in flames is
sobering. Here is the "Cloak and Dagger Attack". It has its own web
site. http://cloak-and-dagger.org/
Here's
a
nice writeup of it on TMP. Some highlights...
In this paper, we will demonstrate how to quietly mount practical, context-aware clickjacking attacks, perform (unconstrained) keystroke recording, steal user’s credentials, security PINs, and two factor authentication tokens, and silently install a God-mode app with all permissions enabled. We note that this behaviour seems to appear to be a deliberate decision by Google, and not an oversight. To the best of our understanding, Google’s rationale behind this decision is that an explicit security prompt would interfere too much with the user experience, especially because it is requested by apps used by hundreds of millions of users. ...none of the users actually managed to understand what happened even after we told them the app they played with was malicious... ...the majority of presented attacks are possible due to inherent design issues... Thus, it is challenging to develop and deploy security patches as they would require modifications of several core Android components.
- UPDATE 2017-04-04 - Google Project Zero tells us what to expect when you rely on proprietary drivers in Android devices. Remote attacks over wifi.
- UPDATE 2017-09-25 - Someone has been messing with Xcode, the Apple development platform used to create iOS apps (and other things). The important point here is that if attackers control the tools that build other software, they control that derivative software too. This corresponds to some Snowden revelations about intelligence agencies going after this target. Here's a long article about that. I would say that it doesn't matter if the CIA or NSA is doing it or Chinese cybercriminals. What matters is that it can be done. You can believe that it is just not possible to safeguard against this level of attacking sophistication, but Linux (proper, not walled-garden Android) says that is wrong. There is no computer science principle forcing us to accept compromised development tools!
- UPDATE 2018-01-16 - Skygofree is malware that can exploit, "Location-based sound recording through the microphone of an infected device – recording starts when the device enters a specified location... Abuse of Accessibility Services to steal WhatsApp messages... Ability to connect an infected device to Wi-Fi networks controlled by the attackers". The shocker for me is that anyone is surprised.
- UPDATE 2018-02-23 - "The Skygofree Android implant is one of the most powerful spyware tools that we have ever seen for this platform. As a result of the long-term development process, there are multiple, exceptional capabilities: usage of multiple exploits for gaining root privileges, a complex payload structure, never-before-seen surveillance features such as recording surrounding audio in specified locations."
- UPDATE 2018-03-06 - The Morning Paper reviews a study about how privacy improves with new app releases. It does not improve! The enumeration and accounting of the privacy violations inherent in typical apps is sobering.
- UPDATE 2018-04-18 - Apple's iPhone wifi sync is an open barn door.
- UPDATE 2020-07-16 -
An article titled:
TikTok
and 32 other iOS apps still snoop your sensitive clipboard data.
There are quite a few others. I'm surprised by all the news sites like
ABC, Al Jazeera, CBC, CBS, Fox, NYT, NPR, The Economist, WSJ, Reuters.
That's so strange to me that I suspect all of these are using some
middleware "news site" product that does this.
And another article, this one for the Android serfs: Google removes 25 Android apps caught stealing Facebook credentials. Although these apps are pretty lame, they had 2.34e6 downloads, so it isn't nothing. Just remember, this is what is neatly served up in the news. If you think that's all of the bad actors sorted out I'd call you naive.
- UPDATE 2021-08-15 - Those wacky people at Amnesty International go into pretty good detail about a phone spying system used by governments to track political dissidents by compromising their phones with commercially available exploits. Citizenlab confirms it. This is an entire category of software called "mercenary spyware". Citizenlab also talks about a Covid tracking app that, "Through a vulnerability in the backend database used by this app, we were able to access the geolocation data of hundreds of thousands of users." Thank goodness criminals could never take advantage of these same inherent flaws!
- UPDATE 2022-04-12 - Many will scoff at my assertion that your telephone is a cow that has left the barn. Sure it is really controlled by a collection of large tech companies (i.e. not you!), but they are careful and won't sell you out, right? In this scary article Krebs talks about EDR attacks. An EDR is an Emergency Data Request used by law enforcement to get information quickly on some serious problem suspect, say, an "active shooter". That's nice; thankfully everyone, psychopaths included, have given all their particulars to these tech companies. The problem is that this lowers the bar for a criminal to compel a big tech company to disclose everything it knows. Now a criminal needs only to compromise a single email account of the dumbest member of law enforcement to target anyone. Using that police email address, they craft a fraudulent EDR to get all the tech company knows about the target. This is precisely the kind of attack that is impossible when you are in control of your own computer and data.
UPDATE 2023-06-15 - This iOS vuln is a real gem. "1 The target iOS device receives a message via the iMessage service, with an attachment containing an exploit. 2 Without any user interaction, the message triggers a vulnerability that leads to code execution. 3 The code within the exploit downloads several subsequent stages from the C&C server, that include additional exploits for privilege escalation. 4 After successful exploitation, a final payload is downloaded from the C&C server, that is a fully-featured APT platform. 5 The initial message and the exploit in the attachment is deleted"
My Absurd Telephone
- Providers and vendors sell tweaked versions of Android that may not properly implement security updates. My phone's Android version is from 2011 though the phone says it's up to date. What could go wrong?
- "Settings -> About Phone -> System updates -> Update Android" -> "Your system is currently up to date."
- "Settings -> About Phone -> Android Version" -> "2.2.2"
- Futex attack vulnerable on Android versions 4.0 through 4.3. So am I immune? Ha.
- Linux is currently on kernel version 4.9. Here's my "up-to-date" phone's Linux kernel.
$ cat /proc/version
Linux version 2.6.32.9 (jinyoung.chon@Sprint14) (gcc version 4.4.1
(Sourcery G++ Lite 2009q3-67) ) #1 Mon Mar 7 11:55:10 KST 2011
- The last 2.6.32.9 kernel was packaged on 23-Feb-2010 15:43. This means that when the vendor compiled this Linux kernel for their Android system, it was already a year old.
- UPDATE 2018-03-13 -
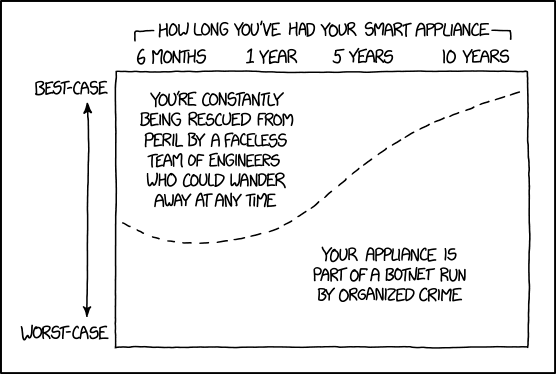
Hover text: "If they're getting valuable stuff from you, at least the organized crime folks have an incentive to issue regular updates to keep the appliance working after the manufacturer discontinues support."
Phones Done Right
UPDATE 2017-10-08 - I have made it clear that today's phones are worse than nothing. Is the technology simply doomed? No. It can be done properly. To understand what is terrible about your phone, check out Puri.sm and their Librem 5 project. What is different about their approach highlights what is painfully unacceptable about Android and IOS (and Windows and OSX for that matter).
UPDATE 2018-06-17 - Gael Duval says "...it's going to be a perpetual game of cat and mouse." But stunningly in this article he's not talking about cybercriminals — he's talking about Google and how they thwart development of open alternatives! He is working on a Google-free Android. Many of the issues discussed in the article highlight why the current status quo smartphone duopoly is so rotten. "Break free from data slavery!" at eelo.
UPDATE 2018-11-05 - While trying to figure out a less rapey way to simply get my files (photos) off a telephone(/camera), I stumbled across https://f-droid.org/ which seems pretty wholesome. (I did select an FTP server for the telephone which did allow me to rescue the files without resorting to my previous method of writing a file uploading server using HTTP/CGI.) Looking over https://f-droid.org/en/about/[f-droid] gives one a good sense for what is horribly wrong with the normal way software on Android and iOS is done.
UPDATE 2019-04-17 - I just came across zerophone.org the existence of which provides many clues to what is wrong with normal phones. Interestingly I found this as I was embarking on my own solution to have a Raspberry Pi "telephone" solution where I was in control.
UPDATE 2019-07-22 - Here's a strange post by Bruce Schneier. What's strange about it is not the fact that backdoors were found built into the firmware of Android devices. No, I've been saying that for years, haven't I? Not a bit surprising. What's odd is that this was apparently done in 2017. Why was the post now? Just being discovered? Ah, just being admitted to by Google now. But is your telephone compromised by malware? In my opinion it is wise to believe the answer is yes.
And xkcd right on target as always.
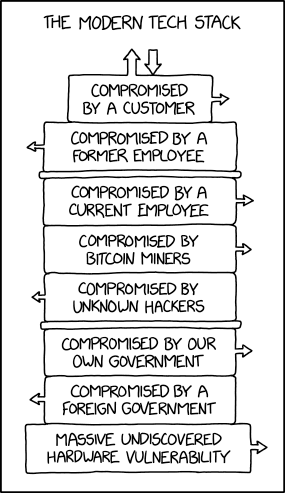
UPDATE 2020-12-06 - Edward Snowden describes the problem pretty well. He mostly covers the creepy side of smartphones which is completely legal. Probably in a way that should be reconsidered. Oh and here's a cheery story of some police state hijinks featuring some political dissidents who thought their phones were not being watched by Big Brother's thugs who could and would torture them. Fun!
UPDATE 2022-04-11 - A lot of people don't really care if surveillance capitalism is constantly creeping on them. Or at least they think that. John Oliver has an extremely excellent piece on data brokers that should make it clear why modern telephone insecurity is actually an important topic.